Lossless embedding: A visually meaningful image encryption algorithm based on hyperchaos and compressive sensing
Xing-Yuan Wang(王興元) Xiao-Li Wang(王嘵麗) Lin Teng(滕琳)Dong-Hua Jiang(蔣東華) and Yongjin Xian(咸永錦)
1School of Information Science and Technology,Dalian Maritime University,Dalian 116026,China
2Guangxi Key Laboratory of Multi-source Information Mining&Security,Guangxi Normal University,Guilin 541004,China
3School of Computer Science and Engineering,Sun Yat-sen University,Guangzhou 511400,China
4School of Cyber Security,Qilu University of Technology(Shandong Academy of Sciences),Jinan 250353,China
Keywords: chaotic image encryption,compressive sensing,meaningful cipher image,portable network graphics,image encryption algorithm
1.Introduction
With the rapid development of big data technology, the amount of data transmitted in the network is also increasing rapidly.As the mainstream form of multimedia information transmission, digital image is widely used in industry, military, medical, and other fields.At the same time, with the increasing security requirements of modern applications, the security of digital image has also attracted people’s great attention.As an effective means to protect digital image information, a large number of image encryption algorithms have been proposed.[1-3]
At present, image encryption technology is mainly divided into two categories.The first category is the traditional image encryption algorithm.That is, the plain image is processed and converted into a noise-like cipher image.Many scholars propose different image encryption schemes based on quantum computation,[4,5]chaos theory,[6-8]fractal sorting matrix,[9-11]DNA coding,[12,13]fractal control theory,[14-16]and other technologies.[17-19]Specifically, this type of image encryption algorithms is mainly composed of scrambling and diffusion, which encrypt the image by changing pixel position and pixel value, respectively.However, the noise-like cipher image generated by such algorithms are easy to attract the attention of hackers and thus suffer from various malicious attacks.The other is the visual image encryption algorithm,[20-24]which first converts the plain image into a noise-like image,and then embeds it into the carrier image to generate a visually meaningful steganographic image.Compared with traditional image encryption schemes,the steganographic images are not easy to attract hackers’ attention during transmission,thereby reducing the possibility of being attacked.Therefore,the research on the visual image encryption algorithm is of great significance.
Baoet al.[25]first proposed a visual image encryption algorithm composed of pre-encryption and embedding process,which can not only protect the security of the content carried by digital image, but also reduce the possibility of being attacked.Unfortunately, the volume of steganographic image generated by this scheme is four times that of the plain image,which leads to the extra transmission bandwidth and storage space.However,improved schemes have been proposed.Chaiet al.[26]used compressive sensing to encrypt and compress the plain image,and then embedded the cipher image into the carrier image to generate steganographic image with the same size.Then, Wanget al.[27]proposed an embedding scheme based on least significant bit(LSB)and integer wavelet transform.The embedding and corresponding extracting process in this scheme are completely reversible.Subsequently, in order to improve the robustness of the encryption algorithm,Zhuet al.[28]proposed a visually meaningful image encryption algorithm based on singular value decomposition embedding.The cipher image was embedded into the diagonal matrix obtained by preforming singular value decomposition on carrier image.In addition,some embedding methods based on pixel value differencing,[29]histogram shifting,[30]reversible color transform,[31]Schur decomposition,[32]most significant bit[33]and others[34-36]were also proposed.Although the existing visually meaningful image encryption algorithms have greatly improved the visual security,there are also some problems: Embedding the cipher image into the carrier image will destroy the pixel structure of the carrier image,and affect the imperceptibility of the steganographic image.There is truncation error in the encryption process, which will decrease the quality of the decrypted image.The extracting process requires the carrier image, which requires additional storage space and transmission cost.
In order to solve these problems,this paper proposes a visual image encryption algorithm combining hyperchaotic system, compressive sensing and PNG-based embedding.The proposed algorithm consists of two main stages.In the first stage, DWT is applied to plain image.Meanwhile, the hash value of plain image is used to control the hyperchaotic system to generate scrambling and measurement matrix.Then the sparse matrix after threshold processing is encrypted and measured by dynamic spiral block scrambling and compressive sensing to obtain the cipher image.In the second stage, the cipher image is embedded into the alpha channel of the PNG carrier image to obtain a visually meaningful steganographic image.Moreover,the embedding position of cipher image elements is controlled by chaotic sequences.The prominent contributions of this paper are as follows:
(i) A lossless embedding method and dynamic spiral block scrambling are designed for visual image encryption.
(ii) The proposed visually meaningful image encryption algorithm has very high visual security.Additionally,the quality of decrypted image is independent of the carrier image.Therefore,the carrier image can be selected flexibly.
(iii) Our encryption algorithm can effectively resist the chosen-plaintext attacks by associating with the hash value of the plain image.
(iv)The proposed decryption algorithm can extract the cipher image blindly,which effectively reduces the transmission cost and storage space.
The rest of this article is organized as follows.In Section 2 we introduce the relevant knowledge.In Section 3 wedescribes in detail the image encryption and the corresponding decryption algorithm.The simulation experiments and performance analyses are given in Sections 4 and 5.In Section 6,we compare the proposed algorithm with other existing visual image encryption algorithms.Lastly,we present a concise conclusion in Section 7.
2.Relevant knowledge
2.1.Hyperchaotic Lorenz system
In this paper, the hyperchaotic Lorenz system is used to generate the pseudo-random sequences, and its dynamic equation[37]is expressed as follows:
wherea,b,c, andrare the control parameters of the system.Whena=10,b=8/3,c=28, andr=-1, the system is in the hyper-chaotic state,and the corresponding Lyapunov exponents areλ1=0.3381,λ2=0.1586,λ3=0,λ4=-15.1725.In our scheme, four chaotic sequences are generated for encryption and embedding.
2.2.Compressive sensing
Compressive sensing(CS)is used to simultaneously sample and compress signals.According to the theory,if the signal is sparse,it can be reconstructed with less sampling data.[38]
Suppose that a one-dimensional signalx ∈Rncan be represented by a set of linear combinations of sparse basisΨT={ψ1,ψ2,...,ψN}.This process is denoted by
wheresi={s1,s2,...,sN}is the coefficient vector of signalx.When the signalxhas onlyK(K ?N) nonzero coefficients on a certain basisΨ,Ψis called the sparse basis of the signalx,andsis the sparse coefficient.
The signalxis projected onto a set of measurement matricesΦto obtain the measurement valuey.That is,anM×N(M<N) measurement matrixΦ, which is not related to the sparse basis matrix, is used to linearly project the signalxto obtain the linear measurement valuey.This process is expressed by
Since the signalxcan be sparsely represented:x=Ψs, the above formula can be rewritten as
whereΘis called the sensing matrix.When the matrixΘsatisfies the RIP criterion,[39]the reconstruction process of the signalxcan be transformed into an optimization problem under the minimum norm ofl1,
At present, the commonly used effective reconstruction algorithms include matching pursuit(MP),orthogonal matching pursuit(OMP),gradient projection(GP),smoothl0norm(SL),and so on.Because the smoothl0norm has the characteristics of low calculation amount,high estimation accuracy,and strong robustness.It is selected as the reconstruction algorithm in this paper.
2.3.Generating measurement matrix
When the signal is sparse in the transform domain, the original signal can be compressed by the measurement matrixΦ.The hyperchaotic Lorenz system is used to generate measurement matrix in this paper.The specific generation steps are as follows:
Step 1 The initial valuesx,y,zandware used to iterate the hyperchaotic Lorenz system for 1000+mNdtimes,and the first 1000 values are discarded to obtain a chaotic sequenceX,
where parameterdis the sampling interval.
Step 2 The chaotic sequenceXis sampled equidistantly to obtainX',This process is denoted in Eq.(7).
Step 3 To map the range of sequence values to(-1, 1),the sequenceX'is processed by using the following equation to obtain a new sequenceX'':
Step 4 The obtained sequenceX''is reordered in a column-wise manner,and then the measurement matrixΦm×Nis constructed as
2.4.Dynamic spiral block scrambling
Spiral scanning can be used to scramble the plain image, which can interfere with the high correlation between image pixels to increase the security level of the encryption algorithm.However, the traditional spiral scrambling has its limitation.After scrambling,the value of the special position in the matrix remains unchanged, such as the position of the number 9 in Fig.1.In addition,some classical scrambling algorithms, such as Arnold transform, have periodicity, which means that the image will return to the original image after a certain number of transformations.In order to solve these problems and to achieve better scrambling effect, a new dynamic spiral block scrambling algorithm is proposed in this paper.This method not only ensures the security of the algorithm, but also changes the positions of all pixels in only one round of encryption.The specific steps are as follows:
Step 1 Select the appropriate lengthN0to divide the image with size ofM×NintoNSsub-blocks with size ofN0×N0,the number of sub-blocks is expressed by
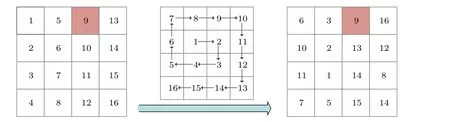
Fig.1.4×4 matrix transferred spiral scrambling process.
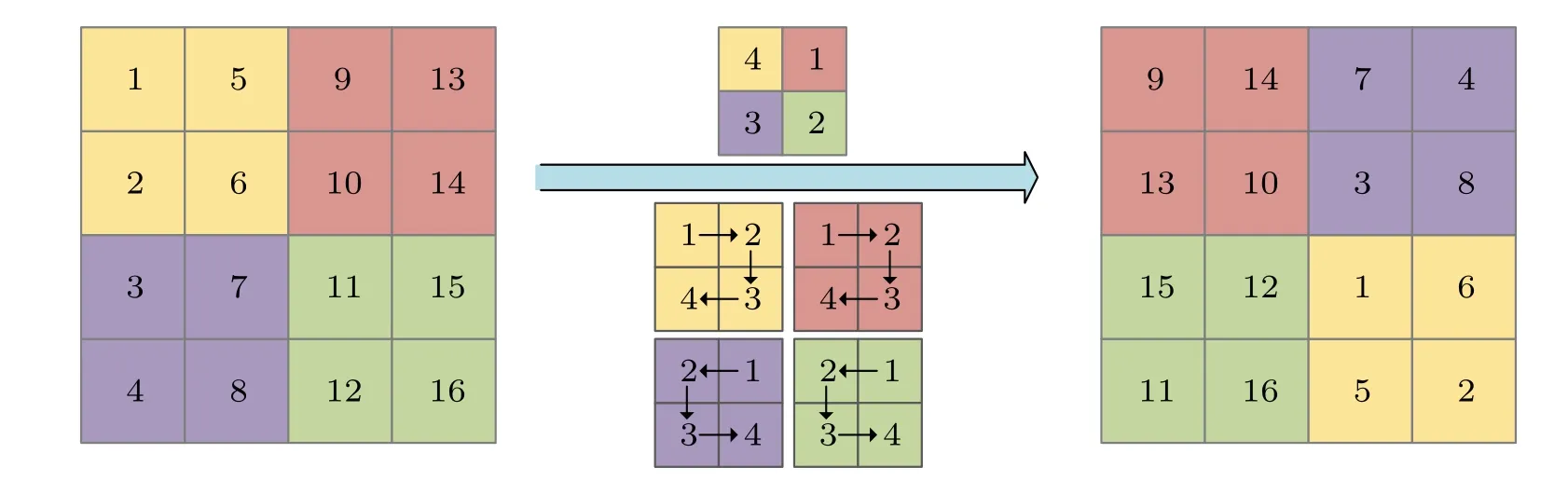
Fig.2.A 4×4 matrix transferred by dynamic spiral block scrambling via a 2×2 sub-block.
Here,represents the smallest integer value not less thanx.IfN0cannot divide the length and width of the image, the image is filled in the shortest sequence, which is randomly composed of integers between 0 and 255, and the number of sub-blocks is determined.
Step 2The chaotic sequenceYwith length ofNSis used to scramble the pixels in the sub-block.IfYiis odd, a clockwise spiral scrambling is performed on thei-th sub-block matrix.On the contrary,a counterclockwise spiral scrambling is performed.
where ceil (x) represents the smallest integer value not less thanx.
Step 3Sort the chaotic sequenceYwith length ofNSin ascending order to obtain the scrambling sequenceS1,and useS1to exchange the positions of the sub-blocks,
Due to the different pseudo-random sequences generated,the scrambled matrix is also different.The algorithm can change the position of all pixels with only one scrambling.For example,a 4×4 matrix is divided into four 2×2 sub-blocks,and then the process of dynamic spiral block scrambling is shown in Fig.3.
2.5.Portable network graphics
Portable network graphics (PNG) is a bitmap graphics format that can represent images lossless.It consists of an 8-byte PNG file signature field and more than 3 subsequent data blocks(IHDR,IDAT,IEND).PNG is designed to replace the two file formats GIF and TIFF.At the same time,it also adds some features that the GIF file format does not have, such as supporting for transparency.PNG can define 256 transparency levels for the image, allowing the edge of the color image to blend smoothly with any background,and because of this,the jagged edges of the image are completely eliminated.Because of the characteristics of small size, lossless compression and better network transmission display, PNG is widely used as information transmission media in the network.
3.Algorithm description
3.1.The encryption process
The flow chart of the encryption scheme proposed in this paper is shown in Fig.3.The algorithm mainly includes two stages.In the first stage,the plain image is encrypted and compressed by dynamic spiral block scrambling and compressive sensing to obtain the cipher image.Then,in the second stage,the cipher image is embedded into the alpha channel of the PNG carrier image to generate the steganographic image.
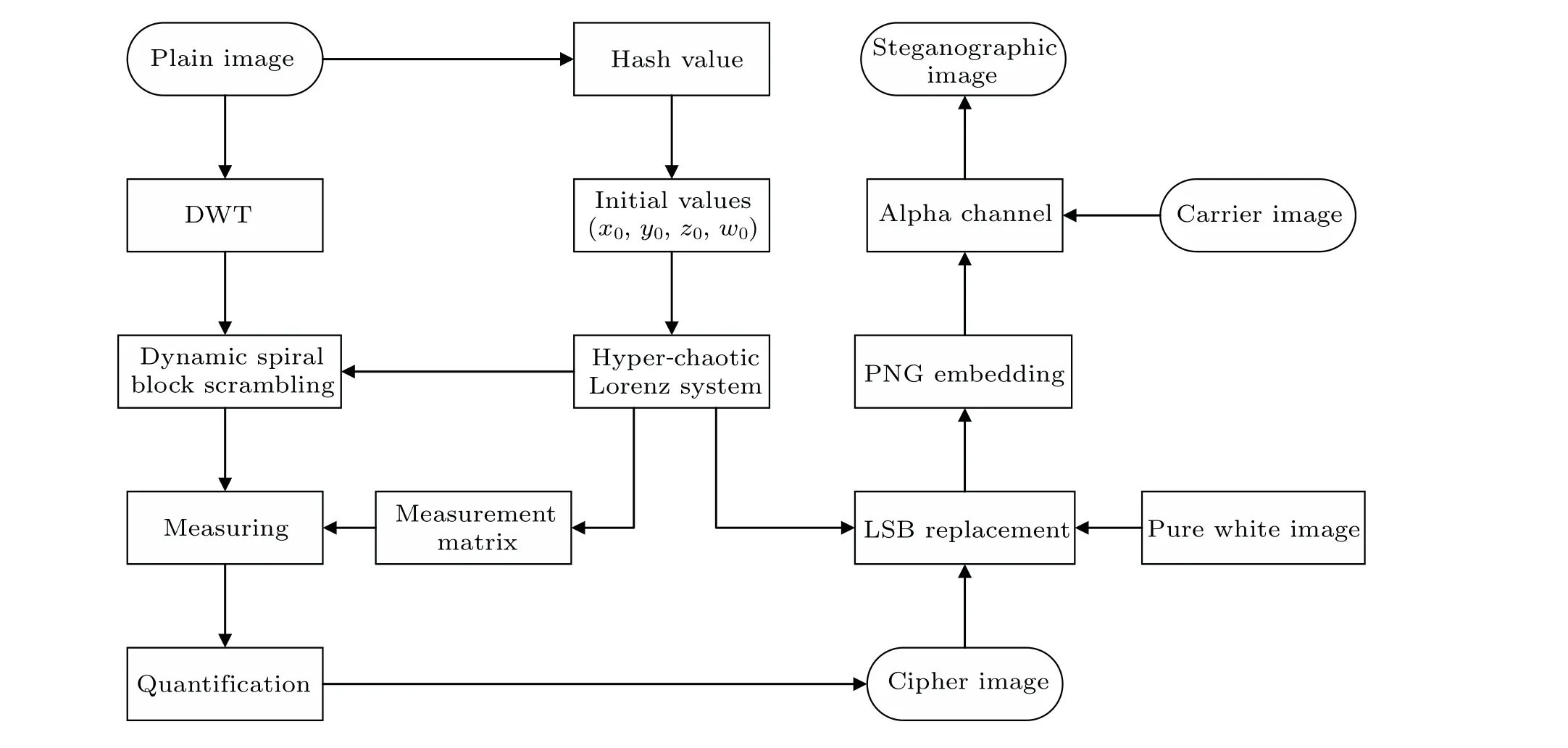
Fig.3.The flow chart of the proposed encryption algorithm.
In the encryption process,the hash value of plain image is used to generate the initial values of the hyperchaotic Lorenz system, and then the hyperchaotic system is utilized to construct measurement matrix, scrambling sequence and embedding sequence.Assume that the size of the plain imagePand the carrier imageCare bothM×N.
3.1.1.Generating the cipher image based on dynamic spiral block scrambling and CS
Step 1Perform the hash algorithm on the pixel values of the plain imagePto generate 256-bit hash value and represent it as hexadecimal numberH.Each 16-bit hash value inHis processed according to Eq.(13)to generatek1,k2,k3andk4,
Step 2Calculate the average value of all pixels of the plain imagePand normalize to getr.The formula is given in the following.Thenk1,k2,k3,k4, andrare used to calculate the initial valuesx,y,z,wof the hyperchaotic system.This process is also given in the following:
Step 3Use the initial valuesx0,y0,z0,andw0to iterate the hyperchaotic Lorenz system 1000 times and discard these values (to avoid transient effects).Continue to iterate to get the chaotic sequencesX,Y,Z,andW.We have
Step 4Use the discrete wavelet transform to sparse the plain imagePto obtain the sparse coefficient matrixP1with the same size.This process is expressed as
whereΨis the orthogonal wavelet matrix,andΨ'is its transposed matrix.
Step 5If the absolute values of the coefficient matrixP1are less than or equal to the setting threshold,these values are forced to be set to 0 to obtain the matrixP2.The chaotic sequenceYand the scrambling sequenceS1are used to perform the dynamic spiral block scrambling on the matrixP2,and the scrambling coefficient matrixP3is obtained.
Step 6The chaotic sequence generated by the hyperchaotic Lorenz system is used to generate the measurement matrixΦwith size ofm×N,wherem=×M」,andCRis the compression rate set by the user.The specific construction process is described in Subsection 2.3.
Step 7Use measurement matrixΦto measure matrixP3,the compressed matrixP4with size ofm×Nis obtained.The measurement formula is
Step 8Quantize the measurement value matrixP4to the range of 0-255 according to the following equation,the cipher imageP5is obtained.
where max and min represent the maximum and minimum of matrixP4,respectively,and floor(x)represents the largest integer not greater thanx.
3.1.2.Embedding the cipher image into the carrier image
Step 1Convert the cipher imageP5into a binary onedimensional array with size ofm×N, denote asE.Take the adjacent two bits of each element inEas a group,store them successively in the low two bits of four binary arrays with size ofm×N,namelyE1,E2,E3,andE4,and set the value of the remaining bits as 0.
Step 2Construct a matrixFwhose size ofM×Nand all the values are 255,and divide it into four one-dimensional arraysF1,F2,F3,F4with size ofm×Naccording to
Step 3Convert the elements in the one-dimensional arrayF1,F2,F3,F4into binary,and set the value of the lower 2 bits of each element to 0 to getF'1,F'2,F'3,F'4.
Step 4Sort the chaotic sequenceWwith length ofm×Nto get the random replacement sequenceS3.The formula is given as follows:
Step 5Replace the lower 2 bits ofF'1(S3(i)),F'2(S3(i7)),F'3(S3(i7)),F'4(S3(i)) with the lower 2 bits ofE1(i),E2(i),E3(i),E4(i).The process can be expressed by
Step 6Convert the elements inF1,F2,F3,F4to decimal,then compose them into a one-dimensional arrayF'with size ofM×N, and finally reshape the one-dimensional arrayF'into anM×NmatrixF''.The formulas for this step are described as follows:
Step 7 WriteF''into the alpha channel of the PNG format carrier image,and finally get the PNG format steganographic imageSwith the same size.
3.2.The decryption process
The decryption process is the reverse process of the encryption process,mainly including extraction and reconstruction.It is worth mentioning that the embedding process and the corresponding extraction process are completely reversible.During decryption, key parameters, such as 256-bit hash value,r,andN,must be sent to the receiver.Figure 4 is the decryption flow chart,the decryption steps are given in the following.
Step 1 Extract the cipher information from the alpha channel of the PNG steganographic imageS, and the matrixF''is obtained.
Step 2 The matrixF''is sequentially divided into four one-dimensional binary arraysF'1,F'2,F'3,F'4with size ofm×N.The sequenceS3is used to perform the inverse random replacement operation to obtainE1,E2,E3,E4,the formula is given as follows:
Step 3 The lower 2 bits of each element inE1,E2,E3,E4are sequentially integrated into the one-dimensional binary arrayEwith size ofm×N.Convert the elements inEto decimal,and reshapeEinto anm×NmatrixP5according to the following equation.P5is the cipher image
Step 4 The inverse quantization process of matrixP5is performed according to the following equation to obtain the measurement value matrixRP4:
Step 5 Generate the measurement matrixΦaccording to the method in Subsection 2.3,and then use the smoothl0norm reconstruction algorithm to obtainRP3fromRP4.This process can be expressed by
Step 6 Use the sequenceYandS1to perform inverse dynamic spiral block scrambling on matrixRP3to generate the matrixRP1.Then inverse wavelet discrete transform(IDWT)is applied toRP1to obtain the final decrypted imageRP.

Fig.4.The flow chart of the proposed decryption algorithm.
4.Simulation results
To verify validity of the proposed algorithm,we carry out experiments on a desktop computer(2.9 GHz i5-9400F CPU,8G RAM), and simulation platform is Matlab R2020a.The parameters during the encryption process are set as follows:d=25,TS=25,CR=0.25,andN=2.
4.1.Encryption and decryption results
Eight gray images with the size of 512×512 are selected as test images in experiment,the results of encryption and decryption are given in Fig.5.Each group of simulation experiments is represented by a column in the graph.The third row is the noise-like secret image obtained by dynamic spiral block scrambling and compressive sensing technology.After embedding the carrier image,the generated steganographic image is visually basically consistent with the carrier image,and has very high imperceptibility.To make the experimental results more convincing, the peak signal-to-noise ratio (PSNR)[40]and the mean structural similarity (MSSIM)[41]are used to quantitatively analyze the imperceptibility of steganographic image and the quality of decrypted image.The experimental data obtained is shown in Table 1,where PSNRdecrepresents the PSNR between the plain image and the decrypted image,and PSNRsteand MSSIMsterepresent the PSNR and MSSIM between the carrier image and the steganographic image.As shown in the table,the PSNRstedata are all greater than 48 dB,and the MSSIMstedata are approximately equal to one.It further verifies that the steganographic image obtained by this algorithm has very high visual security.In addition,the value of PSNRdecis also greater than 35 dB.Because the embedding and extracting process is completely reversible, high-quality decrypted images can be obtained.In a word,the experimental results show that the proposed algorithm generates steganographic image with high imperceptibility, and the decrypted image quality is also very satisfactory.

Fig.5.Simulation results:(a)-(d)are the four plain images Lena,Peppers,Girl and Zelda;(e)-(h)are the four carrier images Barbara,Baboon,Bridge and Goldhill; (i)-(l) are the corresponding secret images, respectively; (m)-(p) are the corresponding steganographic images; (q)-(t)are the respective decrypted images.

Table 1.PSNR and MSSIM values of simulation results.
4.2.Influence of different carrier images on simulation results
In some visual image encryption algorithm based on compressive sensing, the choice of carrier image has a great influence on the quality of decrypted image.In other words,if the carrier image is selected improperly, the quality of the decrypted image will be poor.In addition, different carrier images have a great influence on the imperceptibility of steganographic images.Therefore, the carrier image cannot be selected flexibly.By contrast, the PNG-based embedding method proposed in this paper is to embed the cipher image into the alpha channel of the PNG carrier image, which does not destroy the pixel structure of the carrier image.In order to measure the impact of different carrier images on the quality of the decrypted images in this algorithm, we encrypt the Zelda image with size of 512×512 and then embed it into five different carrier images respectively.The experimental results are shown in Fig.6 and Table 2.It can be seen from the experimental data that different carrier images have no effect on the quality of the decrypted images.The PSNRdecdata are above 37 dB,which indicates that the quality of the decrypted images are very good.In addition, the PSNRstedata are all greater than 48 dB,and the MSSIMstedata are approximately equal to one.It shows that the imperceptibility of steganographic images is very high, and the effect of embedding the same cipher information into different carrier images on the imperceptibility of steganographic images is very small.

Fig.6.Simulation results for plain image Zelda with different carrier images:(a)-(e)are five carrier images Baboon,Goldhill,Couple,Barbara and Bridge;(f)-(j)are the respective steganographic images;(k)-(o)are the corresponding decrypted images.
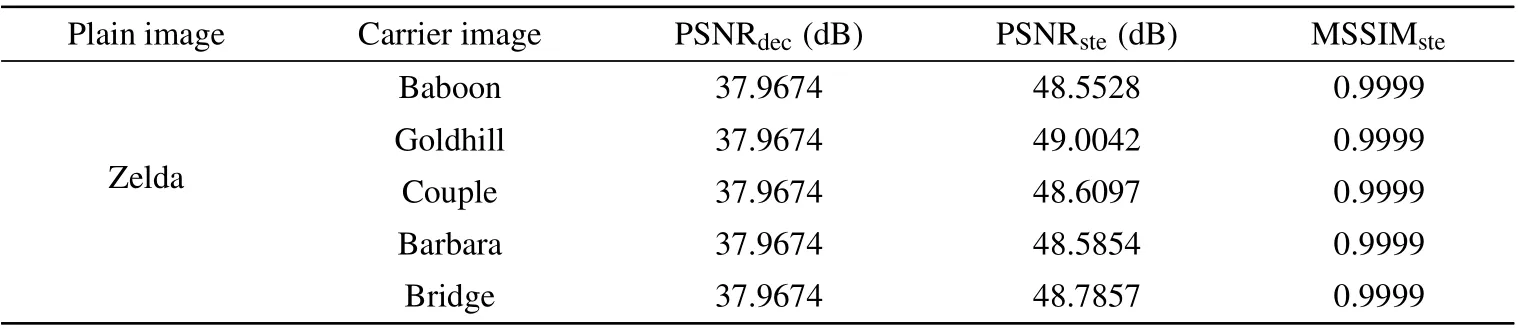
Table 2.PSNR and MSSIM values for different carrier images.
4.3.Influence of important parameters on encryption and decryption performance
In the algorithm proposed in this paper, different parameters may have different effects on encryption and decryption,such as the threshold TS.Next, we analyze the impact of the threshold TS on the quality of the decrypted image.We encrypt the plain images Girl and Woman which sizes are both 512×512,and then embed them into the carrier images Goldhill and Barbara through PNG-based embedding method.At the same time,SL0and OMP reconstruction methods are used to analyze the impact of threshold TS on the experimental effect,and the results are shown in Fig.7.It can be seen from the figure that no matter which reconstruction method is adopted,the PSNR shows a trend of first increasing and then decreasing.Therefore, in order to achieve better decryption quality,the threshold TS should be set at about 20.After the threshold exceeds 20,the quality of the decrypted image will gradually decline.The threshold value has a great influence on improving the reconstruction performance of the image.In addition,it can also be seen from the figure that the SL0reconstruction method is generally better than OMP.
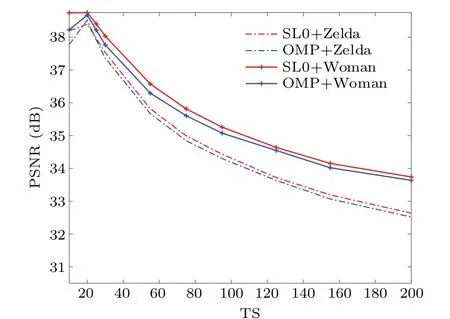
Fig.7.PSNR vs.TS with different reconstruction methods.
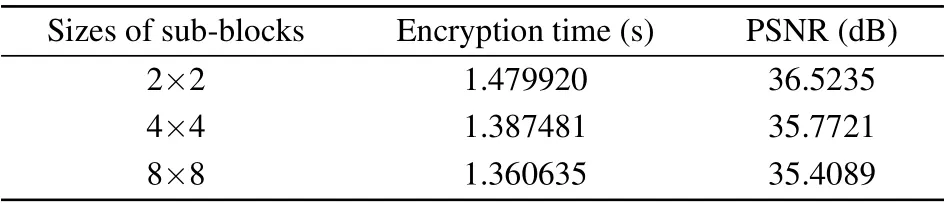
Table 3.Encryption time and PSNR for different sizes of sub-blocks.
In addition,the number of sub-blocks in the dynamic spiral block scrambling algorithm will also affect the encryption and decryption effects.Taking the plain image Lena with the size of 512×512 as an example, the PSNR is used to quantitatively analyze the quality of the decrypted image.The influence of sub-blocks size on the quality of the decrypted image and encryption time is shown in Table 3.Experimental results show that the smaller the sub-block size is,the longer encryption time the algorithm needs.If the sub-block size is 2×2,the encryption time of the algorithm will be relatively long.When the sub-block size is 8×8,the decrypted image quality decreases slightly in comparison.
5.Performance analyses
In this section,we mainly analyze the performance of the proposed algorithm, including key space, plaintext sensitivity, robustness analysis and running efficiency analysis.The parameters used in the experiments are the same as those described in Subsection 4.1.
5.1.Key security analysis
The key space is an important indicator to measure whether an encryption algorithm can resist brute force attacks.Generally speaking,the key space of an encryption algorithm needs to reach 2100.[42]This paper performs hash algorithm on the pixel values of plain imagePto generate a 256-bit hash value,which is used to generate the initial valuesx,y,z,wof the hyperchaotic system.Assume that the computing accuracy of the computer is 10-14.Then the total key space is greater than (1014)4×2256?2100.In addition, there are other keys in the encryption process, such as the sub-block sizeN0and the threshold TS.Therefore,the total key space is much larger than 2100,which is enough to resist various brute force attacks.
5.2.Plaintext sensitivity analysis
A good encryption algorithm should have high plaintext sensitivity,which can be used to measure whether the encryption algorithm can resist the chosen-plaintext attacks.The encryption scheme proposed in this paper uses the hash value of the plain image to generate the initial values of the hyperchaotic system, so the encryption scheme can well resist the chosen-plaintext attacks.The mean structural similarity and the number of pixel change rate (mathematical expression is shown in Eq.(29)) are introduced to quantitatively evaluate the plaintext sensitivity of the algorithm proposed in this paper.
In Eq.(30),C1 andC2 are two images with size ofh×w.
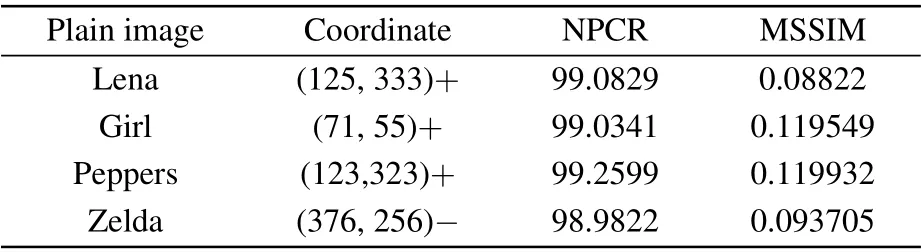
Table 4.Simulation results of the plaintext sensitivity with carrier image Goldhill.
The experimental results are shown in Table 4.Four plain images with size of 512×512 and the corresponding modified plain images are encrypted, and then embed them into the steganographic image Goldhill.In the first row of Table 4,(125,333)+represents that the pixel values of the pixel point(125,333)in the image Lena are added by one.As can be seen from the experimental data,when the pixel values of the original plain image are slightly modified,the NPCRs between the two generated steganographic images are approximately equal to one, and the MSSIMs are close to zero.This shows that the algorithm proposed in this paper has very high plaintext sensitivity.
5.3.Robustness analysis
5.3.1.Noise attack
Considering that steganographic image will be affected by various noises during transmission,such as salt and pepper noise(SPN),Gaussian noise(GN)and speckle noise(SN),the quality of decrypted image will be reduced.In order to better test the ability to resist noise attacks of the proposed scheme,the plain image Girl with size of 512×512 is compressed and encrypted, and then embed it into the carrier image Bridge.SPN,GN and SN of different intensities are artificially added to the alpha channel of the PNG steganographic image.The experimental results are shown in Fig.8.From the quality of the decrypted image,GN has the greatest effect on the encryption scheme,but the figure contour information in the decrypted image can still be recognized.Numerically,when the noise intensity is 0.00001%, 0.00003%, and 0.00005%, the PSNR values are 37.0430 dB, 35.0528 dB, and 29.3540 dB,respectively.In contrast, SPN and SN have little effects on the encryption algorithm.Under the same noise intensity,the PSNR values remain at 37.0430 dB, which further indicates that the proposed scheme can well resist SPN and SN.Conclusively,the proposed encryption scheme has a strong capability to resist SPN and SN,also it can resist GN to some extent.

Fig.8.Robustness test results against noise attack for Girl.
5.3.2.Cropping attack
Steganographic images may encounter malicious cropping attacks by hackers during transmission.Therefore, the proposed encryption algorithm also needs to be robust enough.In this section, we test the ability of the proposed encryption scheme to resist cropping attacks.In the test, the steganographic images with 32×32, 64×64, 100×100 and 120×120 data losses are illustrated in Figs.9(a)-9(d), and the corresponding decrypted images are shown in Figs.9(e)-9(h), the PSNR values are 32.5064 dB, 31.6406 dB, 29.7184 dB, and 29.0634 dB,respectively.It can be seen that when the steganographic image has 120×120 data loss,the peak signal-to-noise ratio between the decrypted image and plain image can still reach 29 dB, and the contour information of the figure in the decrypted image can still be clearly identified.The experimental results show that the proposed image encryption has a strong ability to resist cropping attacks.

Fig.9.Robustness test results against cropping attack for Girl: (a)-(d)steganographic images with cropped 32×32,64×64,100×100,and 120×120,respectively;(e)-(h)decrypted images of(a)-(d)
5.4.Running efficiency analysis
The running efficiency of the algorithm is also one of the indicators to measure the performance of the encryption scheme.In order to realize the real-time image processing,it is necessary to improve the efficiency of the algorithm as much as possible.In this subsection,we analyze the encryption time of the proposed algorithm, and select the plain image Lena with the size of 512×512 and 256×256 for experiment.When the sub-block sizes of dynamic spiral block scrambling are 2×2 and 4×4, the experimental results are shown in Table 5 and Table 6, respectively.Here “encryption” represents the encryption and compression process,and“embedding”represents embedding the cipher image into the carrier image.It can be concluded from the experimental data that,firstly,the embedding process takes up most of the time of the whole encryption process.However,for Lena with size of 512×512,PNGbased embedding process only takes 0.070259 s,and most of the time is spent on LSB replacement.Secondly,the sub-block size of the dynamic spiral block scrambling has a great impact on the Encryption process time.It can be seen from the comparison that if we want to improve the encryption efficiency of the algorithm,the larger sub-blocks should be selected.

Table 5.Encryption time for different images via a 2×2 sub-block(unit: s).
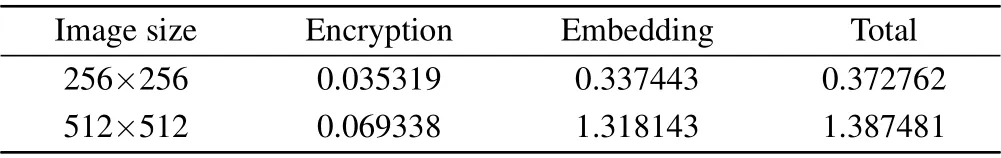
Table 6.Encryption time for different images via a 4×4 sub-block(unit: s).
5.5.Chosen-plaintext attack analysis
UP to now, many encryption algorithms have been attacked by chosen-plaintext attacks.The main reason is that different plain images correspond to the same key stream in encryption.However,in this paper,first the average value and hash value of plain image are calculated and used to generate the initial values of the chaotic system.Then, chaotic sequences generated by hyperchaotic Lorenz system are used for dynamic spiral block scrambling,measurement matrix generation and PNG-based embedding.In this way,different encryption keys are generated for different images, thus improving the ability to resist plaintext attack.
To better prove the proposed algorithm so that it can resist the chosen-plaintext attack,we also carry out experimental verification.This attack can be portrayed as[23]
whereO1andO2are plain images,C1andC2are their corresponding cipher images.If this equation is applied to anyiandj,it means that the test method can resist the chosen-plaintext attack.
To intuitively observe more test results, the plaintext attack of three pairs of gray image pairs is tested.In Fig.10,the first and second columns are plain images, the fourth and fifth columns are their corresponding secret images, and the third and sixth columns represent the XOR of two plain images and the XOR of two secret images, respectively.It is evident that the equation is satisfied, so the algorithm has strong resistance towards the chosen plaintext analysis.In addition,we first perform the XOR operation on two plain images,and then perform the XOR operation on their cipher images.We compare the two images obtained after XOR,calculate the number of different pixels between them, and the proportion of these different pixels in the total pixel number of the cipher image.The statistical results are shown in Table 7.From the above discussion,it is clear that the hacker cannot obtain the key by applying a chosen plaintext attack.

Fig.10.Image-by-pixel XOR operation of two images: (a)plain image Peppers,(b)plain image Zelda,(c)(a)⊕(b),(d)secret image Peppers,(e) secret image Zelda, (f) (d)⊕(e); (g) plain image Lena, (h) plain image Girl, (i) (g)⊕(h), (j) secret image Lena, (k) secret image Girl, (l)(j)⊕(k);(m)plain image Bridge,(n)plain image Goldhill,(o)(m)⊕(n),(p)secret image Bridge,(q)secret image Goldhill,(r)(p)⊕(q).

Table 7.Statistical analysis of chosen-plaintext attack.
6.Comparison with related schemes
In this section, we compare the image encryption algorithm proposed in this paper with existing related algorithms,mainly from the four aspects of visual security,decrypted image quality,robustness,and encryption efficiency.The experimental data are given in the following.In order to make a fair comparison, the experimental data to be compared is directly quoted from the source paper or obtained through simulation experiments.
6.1.Visual security
For visual image encryption algorithms, the imperceptibility of steganographic images is an important indicator to measure its security.The higher the imperceptibility of the steganographic image is,the greater the similarity between the steganographic image and the carrier image is,then the higher the visual security of the encryption algorithm is.In order to quantitatively measure the imperceptibility of steganographic images, we compare the PSNRsteand MSSIMstewith the experimental results of Refs.[26,27].The results are shown in Table 8.
It can be seen from the comparison data that the average PSNRstevalue proposed in this paper is as high as 48.6207 dB, while the average PSNRstevalue of Ref.[26] is only 23.8436 dB.The proposed encryption scheme can also improve the average PSNRstevalue of Ref.[27] by 37.80%.At the same time, the average MSSIMstevalue of the algorithm proposed in this paper has also reached 0.9999, which is much larger than the MSSIMstevalue of Refs.[26,27].In conclusion,the comparison results fully confirm that the algorithm proposed in this paper improves the imperceptibility of steganographic images and has a high degree of visual security.

Table 8.Comparison of PSNR and MSSIM values of steganographic images.
6.2.Decrypted image quality
The embedding process and the corresponding extraction process of the encryption algorithm proposed in this paper are completely reversible.PSNRdecis used to quantitatively compare the quality of the decrypted images,and the experimental data obtained are shown in Table 9.It can be seen from the comparison results that the decrypted image quality of the proposed encryption scheme is much higher than the other,which further confirms that the decrypted image quality of the proposed encryption scheme is very high.three encryption algorithms can resist SN attack to a certain extent.However, when the intensity increases, the algorithm proposed in this paper has better decryption quality.In addition, as can be seen from Table 11, the data loss increases from 16×16 to 80×80,and the quality of the decrypted image generated by our scheme drops by about 5.3 dB, which is less than those in Refs.[27,43].When the cropping mask becomes larger,the encryption algorithm proposed in this paper provides performance gain about 11 dB.To sum up, the proposed image encryption algorithm based on the PNG embedding method can effectively improve the robustness against noise attack and cropping attack.

Table 9.PSNR values for comparison of different decrypted images.
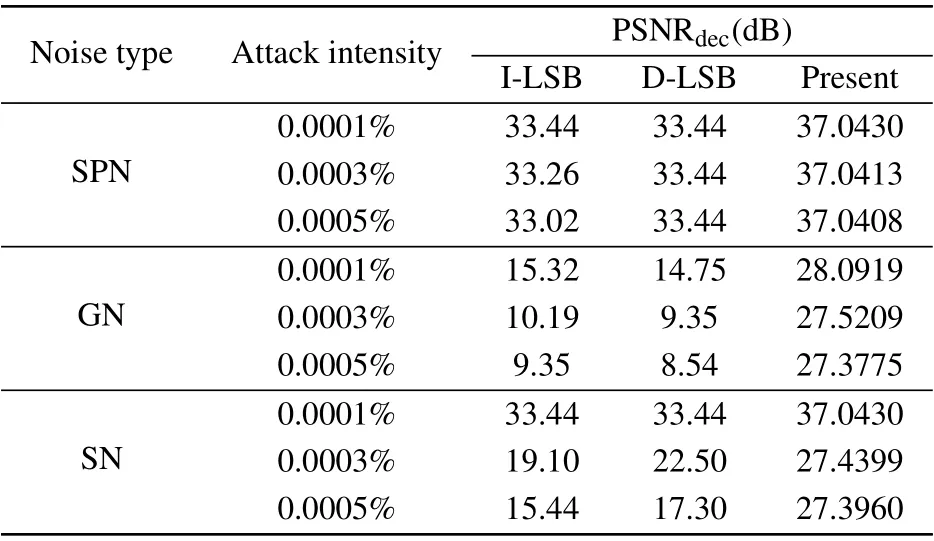
Table 10.Comparison of resistance capability of noise attack.
6.3.Robustness comparison
In this subsection, we compare the robustness of the proposed algorithm with the algorithm based on IWT+LSB embedding[27]and Dynamic LSB embedding.[43]The experimental data comes from Ref.[28].The plain image Girl is encrypted and embedded into the carrier image Goldhill by different encryption schemes.Then add SPN,GN,SN attack and cropping attack of different intensities to the steganographic image.The experimental data obtained are listed in Tables 10 and 11,where I-LSB and D-LSB separately are obtained using the IWT+LSB and dynamic LSB embedding methods.
From Table 10, we can see that no matter which encryption algorithm is used, GN has the greatest impact on the cryptosystem.However,compared with the algorithms of Refs.[27,43],the encryption algorithm proposed in this paper can better resist GN attack.The PSNR values are enhanced approximately 13-17 dB at the same intensity.All the encryption algorithms have strong ability to resist SPN attack.All
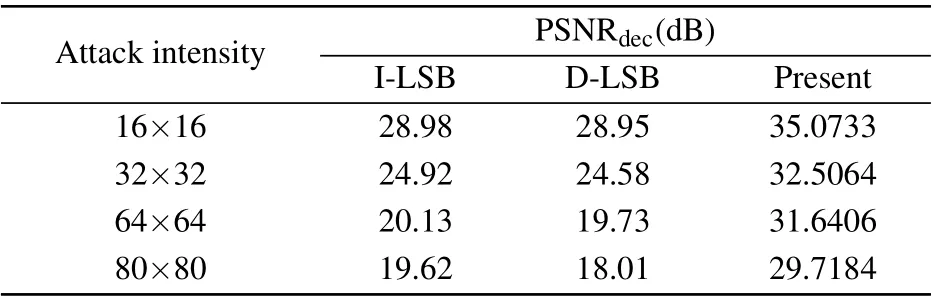
Table 11.Comparison of resistance capability of cropping attack.
6.4.Encryption efficiency
To encrypt the plain image in real time, the encryption time should be as short as possible,the encryption time should be as short as possible.Comparing the encryption efficiency of the algorithm proposed in this paper with Refs.[27,43],the results are given in Table 12.
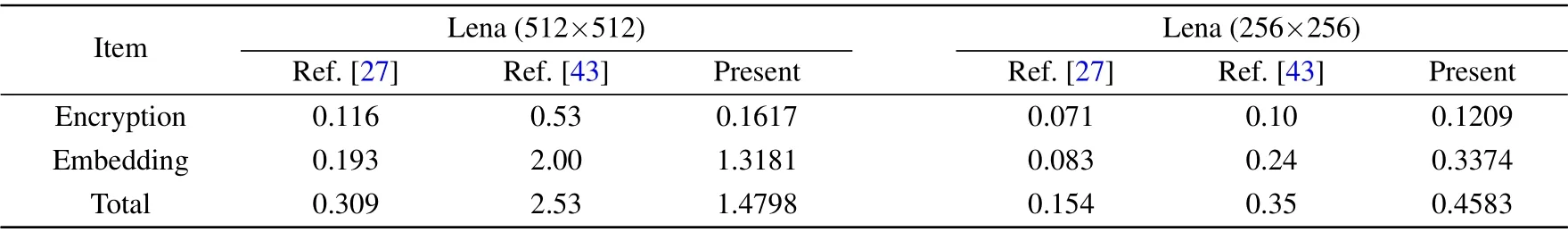
Table 12.The encryption efficiency comparison with other algorithms(unit: s).
The sub-block size of scrambling algorithm is 2×2.As can be seen from the table,when the size of the plain image is 256×256, the encryption time of all algorithms is very short.However, when the size of the plain image is 512×512, the encryption time of Ref.[43] increases dramatically.To sum up,the encryption efficiency of the proposed algorithm is second only to Ref.[27], while the encryption efficiency of the algorithm proposed in Ref.[43]is the lowest.
7.Conclusions
This paper proposes a novel visually meaningful image encryption algorithm combining hyperchaotic system, compressive sensing and PNG-based embedding.In our encryption scheme, dynamic spiral block scrambling and compressive sensing are used to encrypt and compress the plain image.Then the cipher image is embedded into the alpha channel of the PNG carrier image.Different from the existing visual image encryption algorithms,the PNG-based embedding method does not embed cipher image into the pixel,so it does not destroy the pixel structure of the carrier image.The embedding process and the corresponding extraction process are completely reversible, which can avoid truncation errors during embedding and improve the quality of decrypted image.In addition,the proposed decryption algorithm realizes blind extraction,which effectively reduces transmission cost and storage space.Meanwhile, the hash value of the plain image is used to generate the keys, which is beneficial to improve the ability of the proposed algorithm to resist chosen-plaintext attacks.Finally,the experimental results show that the proposed image encryption algorithm has very good visual security,decryption quality and robustness.
It is worth noting that,although existing visual image encryption schemes have good security performance, their embedding positions are usually fixed or controlled by keys.If the embedding position is not appropriate, the imperceptibility of steganographic image may be affected.Therefore, in the future work,we will devote ourselves to studying an adaptive embedding scheme to further improve the security of the algorithm.
Acknowledgements
Project supported by the National Natural Science Foundation of China (Grant No.61672124), the Password Theory Project of the 13th Five-Year Plan National Cryptography Development Fund (Grant No.MMJJ20170203), Liaoning Province Science and Technology Innovation Leading Talents Program Project (Grant No.XLYC1802013), Key R&D Projects of Liaoning Province(Grant No.2019020105-JH2/103),Jinan City‘20 Universities’Funding Projects Introducing Innovation Team Program(Grant No.2019GXRC031),and Research Fund of Guangxi Key Lab of Multi-source Information Mining&Security(Grant No.MIMS20-M-02).
- Chinese Physics B的其它文章
- Matrix integrable fifth-order mKdV equations and their soliton solutions
- Comparison of differential evolution,particle swarm optimization,quantum-behaved particle swarm optimization,and quantum evolutionary algorithm for preparation of quantum states
- Explicit K-symplectic methods for nonseparable non-canonical Hamiltonian systems
- Molecular dynamics study of interactions between edge dislocation and irradiation-induced defects in Fe-10Ni-20Cr alloy
- Engineering topological state transfer in four-period Su-Schrieffer-Heeger chain
- Spontaneous emission of a moving atom in a waveguide of rectangular cross section

